When you send a document for translation, you’re not just moving text from one language to another. You’re transferring sensitive data across systems, borders, and multiple professionals. That creates risk.
At Elmura Linguistics, we’ve worked with legal teams, healthcare providers, financial institutions, and technology companies. Across all sectors, one concern rises to the top: How can we ensure our documents remain secure?
It’s a valid question. Poorly managed translation workflows can expose contracts, personal data, product specs, or internal communications to unauthorized access. And once that data is out, it’s out for good.
If you’re working with confidential or regulated content, secure translation isn’t a nice-to-have. It’s a baseline requirement.
Table of Contents
ToggleVulnerabilities in the Translation Lifecycle
Most data breaches during translation don’t happen because of bad intent. They happen because of bad systems.
Every stage your document passes through introduces risk, especially if you’re working with a provider that lacks structured protocols.
Many translation agencies rely on fragmented workflows, third-party freelancers, unsecured email transfers, and cloud platforms without proper controls.
To help visualize where threats typically arise, here’s a breakdown of common security weak points in the translation process:
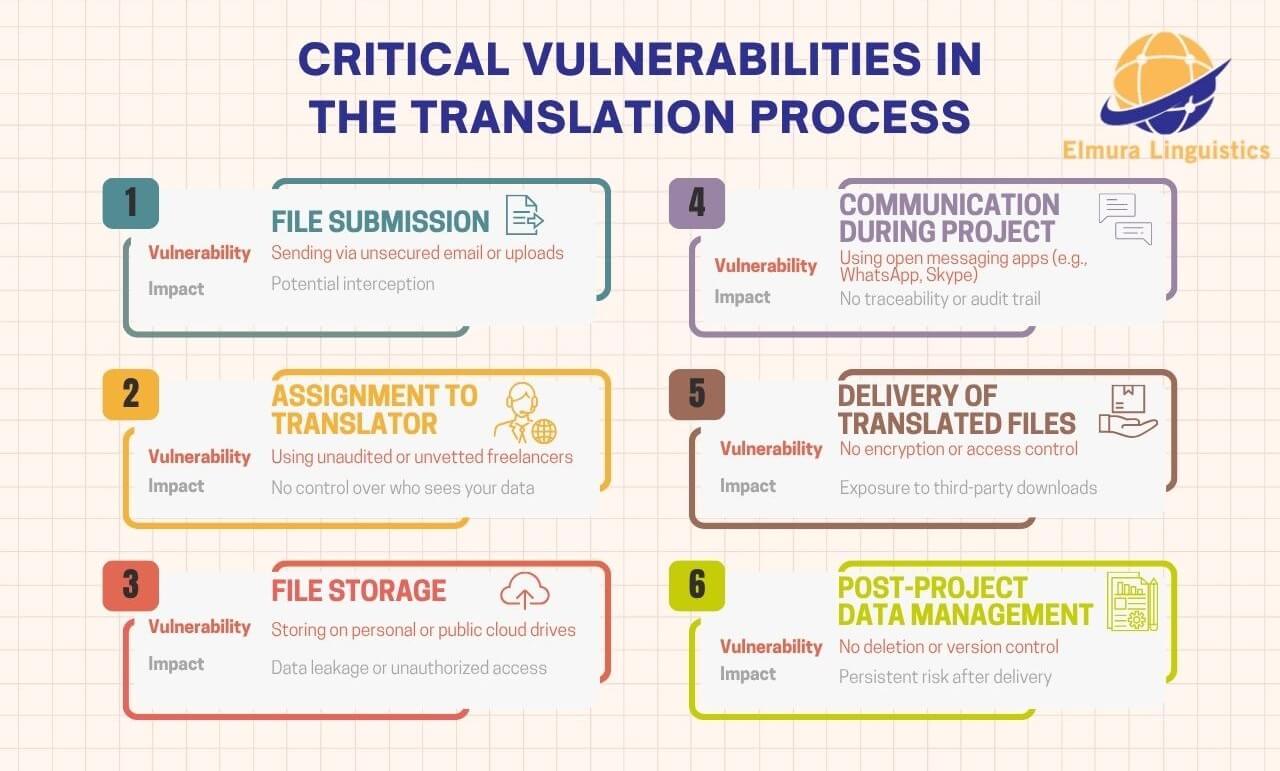
We’ve studied these weak points closely. That’s why we designed a system where each phase is tightly controlled, monitored, and encrypted. No phase is left to chance. No data is passed around loosely. Every handoff is intentional, logged, and limited.
Without this level of oversight, translation becomes one of the easiest ways for sensitive data to slip through the cracks, and into the wrong hands.
Human-Centric Safeguards: Vetting, NDAs, and Access Control

We treat human oversight as the first layer of defense. Every linguist, editor, and project manager we work with signs strict non-disclosure agreements before handling client documents. These contracts are not just formalities. They are enforceable legal instruments that set expectations and accountability from day one.
We also don’t outsource projects to anonymous freelancers. All translators are carefully vetted through a structured screening process. We check qualifications, previous work, and professionalism before they join our network.
Access to sensitive content is always limited. We never allow open distribution of documents across multiple hands. Only authorized personnel are assigned to each project, and we restrict access to only the files they need to complete their task.
We assign responsibility clearly and keep records of who handled each file and when. This approach minimizes exposure and adds full traceability to every project.
Tech That Protects: Infrastructure and Encryption Standards

We use secure infrastructure at every stage of the translation process. Files are never sent over email or stored in generic cloud drives. All file transfers take place through encrypted channels using HTTPS and SFTP protocols.
Our internal systems run on hardened servers with multi-layered firewalls and intrusion detection tools. These systems are actively monitored, not just passively protected.
@umacodes HTTPS is the secure protocol that encrypts data in transit, protecting it from interception and tampering. 🔐 Here’s what happens behind the scenes—breaking down the roles of session keys, private keys, and public keys! #coding #programming #https #cybersecurity ♬ original sound – Uma Abu
We encrypt every file at rest and in transit. That includes source documents, translations, and reference materials. If a file is intercepted, it remains unreadable without the right credentials.
Access is protected through two-factor authentication and permission-based roles. No team member can see content outside their assigned task.
We also have automated data deletion protocols. Once a project is complete, files are removed after the agreed retention period. Nothing stays longer than necessary.
Built-In Security: How Our Platforms Reduce Risk

We’ve designed our client portal and internal project tools with privacy in mind. When you log in, you’re entering a controlled environment. Sessions are protected by two-factor authentication. File uploads and downloads happen inside a secure interface with real-time encryption.
You never need to email documents or rely on third-party file-sharing tools. Our platform keeps all content in one monitored space. Each user’s actions are logged automatically. That includes file views, edits, comments, and downloads.
Permissions are role-based. If someone doesn’t need access, they don’t have it. You control who can see what, and for how long.
We also use version control. Every change is tracked and recoverable. There’s no confusion about which file is final or who modified it.
File Security Within the Elmura Platform
| Stage | Security Feature |
| Login & Authentication | Two-factor login
Session timeout control IP activity tracking |
| File Upload | Encrypted file transfer (SFTP/HTTPS)
Automatic virus scanning |
| User Permissions | Role-based access levels
No default or open access |
| Activity Logging | View and download tracking
Time-stamped edit history |
| File Storage & Versioning | Encrypted cloud storage
Real-time backups Full version control |
| Post-Project Cleanup | Auto-expiry of files after set retention period
Permanent deletion upon request |
Certifications and Compliance That Back It All Up

We hold ISO 27001 certification. This standard confirms that our information security management system meets strict global requirements. It covers how we handle access, encryption, risk response, and data governance.
We also comply with GDPR for all projects involving personal data from the EU. This includes data minimization, consent management, and lawful processing.
For clients in regulated sectors, we follow specific industry rules. That includes HIPAA safeguards for healthcare, confidentiality for legal work, and retention policies aligned with financial compliance.
We submit to regular external audits. These reviews examine our systems, controls, and documentation. We pass them because we build our operations around them.
Final Check: How to Vet a Secure Provider (and Why We Exceed It)

Choosing a secure translation service means asking the right questions. Here’s what you should verify before trusting any provider with sensitive documents:
| What to Ask | Why It Matters |
| Do you have ISO 27001 or similar certifications? | Confirms audited, structured data protection |
| How are translators vetted and bound to confidentiality? | Prevents leaks through unauthorized individuals |
| What tools do you use to transfer and store files? | Reveals encryption standards and storage practices |
| Do you restrict access based on roles? | Limits unnecessary data exposure |
| How do you handle data deletion after a project? | Ensures no lingering risk after delivery |
| Can you support industry-specific compliance needs? | Required for legal, medical, and financial content |
A secure translation provider should offer transparency, documented processes, and proven infrastructure. We do all three. That’s how we protect your content and your trust.
FAQs: Secure Document Translation
Conclusion
Document translation should never expose your business to unnecessary risk. Security must be built into every part of the process, from the tools you use to the people you work with.
We don’t expect you to take our word for it. We invite scrutiny, provide documentation, and operate under strict compliance. If you’re looking for a partner that treats your content like it’s their own, you’re in the right place.
Our platform, policies, and people are aligned to protect what matters most: your information.





